-
Singapore
Copyright © 2025 Powered by BCI Media Group Pty Ltd
Confirm Submission
Are you sure want to adding all Products to your Library?
Contact Detail
06 May 2020 by Carlo Gavazzi Automation

Nowadays, cybersecurity in industrial, commercial and residential installations is a source of concern: cyber-threats and attacks increase day by day, and a drastic rise of IT security incidents is reported by the Governmental institutions like ICS-Cert or BSI. Awareness about cybersecurity issues is mandatory to guarantee the availability of system functionalities, confidentiality of data & protection of intellectual property, integrity of the application function & components in use and authenticity of controllers & their data.
Cybersecurity is a process, not a product. Security improvements need to be continuously maintained and updated. For these reasons, security is not 100% achievable. Even when designed with state-of-the-art security measures, the connections to the networks of suppliers, contractors, and partners of a system may still be vulnerable.
Mitigation of cybersecurity threats is a task that concerns all the parts and parties of an energy monitoring and building automation installation. An effort is requested at different levels for:
• Warranting physical access control to security critical installations
• Providing additional processing power on devices (i.e. for encrypting data)
• Dedicating huger configuration effort for the system integrators and installers
• Planning and executing security training for system integrators and operators
• Training end-users to increase their awareness
Each company must find the right balance about expected cybersecurity goals and relevant investments, and costs. Therefore, manufacturers of data/control automation products have to provide appropriate means of protecting critical parts of their products to system integrator, operator and end-users. Carlo Gavazzi Universal Web Platform embeds several measures as described in “Available Onboard security measures”. These measures do not and cannot replace the responsibility of the system integrator or operator about the application of the security tasks, such as the indication of threats and the definition of necessary measures in order to achieve the desired level of security.
The purposes of an energy monitoring or building automation environment are mainly to measuring data, managing information and operating the necessary control tasks with reliability. However, there are so many risks that can preclude or damage the security of an environment parts. The assets of an Energy Monitoring or Building Automation system are FIELD devices (sensors, meters, actuators), EDGE devices (gateways, controllers, responsible of connecting and controlling a subset of field devices among them and to the upper levels), FOG subsystems (in charge of data automation or control tasks over a specific area) and CLOUD subsystem (in charge of empowering data/control automation with the scalability provided by cloud resources). Both single assets and systems can be compromised by cybersecurity issues at different levels.
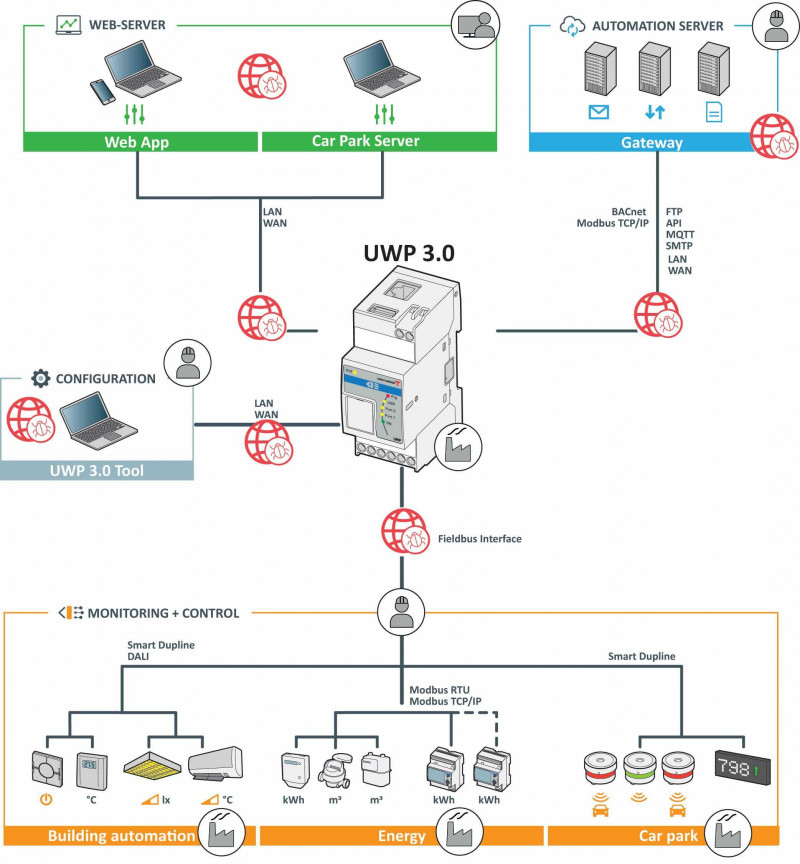
The operational functions executed on the controller are the purpose of an energy monitoring or building automation environment. It is deployed into Carlo Gavazzi Universal Web Platform through its programming software. The EDGE unit also referred to as Controller or Gateway is the programmable intelligent device and the core of the system. The EDGE unit executes locally the automated tasks for controlling actuators or automating data management. It is the major target for security attacks and its protection and communication interfaces are priority for system integrators, operators and end-users. The environments of data/control automation systems have to be able to prevent intended or unintended faulty operations and thus the risk asset harming. Nevertheless, every system needs access during the installation, the commissioning, the operation, or the maintenance. If the whole system is split into subsystems, only authorized personnel has to be allowed to access every subsystem.
Even if cybersecurity is a global concern, there is not a universally-recognized standard. However, threat recognition and countermeasures are usually shared by different standards. The worldwide accepted IEC 62443 standard defines five different levels of security:
The operational functions of an industrial automation system can be damaged or interrupted in different ways. Security measures focus on intentional threats such as sabotage, vandalism or spying although until now unintentional malfunctions caused by faulty hardware, software, commissioning or service have often harmed the assets, and must be taken into consideration while designing the system. Any energy monitoring or building automation is a component of a local or wide-area network, so the following security measures such as anti-virus protection, strong password policies, firewall protection, VPN tunnels for inter-network connections and careful management of removable storage devices should be valid for all standard PCs. Besides, a well-defined user account management for accessing the system and its interconnecting networks is mandatory. Placing the gateway/controller in a protected environment is mandatory to avoid undesired access to the controller or its application.
A protected environment is achievable thanks to the following measures:
• Physical locking. Locked cabinets with no chances of directly accessing the protected units.
• Managed LAN. The intranet network has well-defined user rights and no direct access from outside.
• VPN access. Internet access protected by a firewall and VPN tunnelling. Moreover, the following additional practices are needed:
• INDEPENDENCY. Keep the trusted network as small as possible and independent from other networks.
• FIELDBUS PROTECTION. Protect the cross-communication of controllers and the communication among controllers and field devices via standard communication protocols (fieldbus systems) by appropriate measures. Very often, they are not protected by additional measures, such as encryption. An open physical or data access to fieldbus systems and their components is a serious security risk.
• LOCKING. Lock such networks and strictly separate them from commonly used access.
Cybersecurity is a process, not a product. A great part of the reported security accidents is caused by faulty set-up or system operation. System integrators and end-users have a crucial role concerning the security protection. Thus, both have to know the possible threats and the infra-structural measures necessary to avoid those threats. In order to achieve this goal, it is advisable to join special training by security specialists. Several active parties and suppliers are involved in setting-up and operating an energy monitoring or building automation system. They are mainly the suppliers of software & hardware components, system integrator or builder of the industrial control applications and operators. All of mentioned parties have to make a certain effort in order to protect the application against attacks. A system is as secure as the weakest part. A lacking training to end-user could compromise the most secure installation.
Nowadays cyberthreats assume many different shapes: criminal cyberattacks, malware, social engineering. The vulnerabilities of products and systems, wrong behaviours of users, insufficient security policies and increasing presence of hacking tools and unethical hackers are potential variables have made it not possible to reach 100% cybersecurity. Cybersecurity is not only about devices: it is about people leveraging on social networks and habits. For those reasons while a company defines its approach to cybersecurity, the target is finding the right balance between the acceptable risks and the mandatory countermeasures.
Carlo Gavazzi Automation has defined 4 main pillars of cybersecurity. They are TECHNOLOGY: we always use trusted technologies and best-in-class software and firmware stacks in all of our products, PEOPLE: we allocated a Cybersecurity Team in our R&D, which undergoes a process of recurrent training to adopt best-practices for designing software and firmware, being updated about the evolution of cyber threats, PRESENCE: our organization is present in 23 Countries, and our products sold everywhere: we receive and collect tons of feedback that we use to improve and harden our products & TRUST: we realize that nobody can fight cyberthreats alone.



